Cybersecurity Risks in Legacy Rail Fleets: Why Older Trains Still Matter
As rail operators and train owners invest in new fleets with advanced digital systems, it’s easy for attention to move away from legacy rolling stock. But when it comes to cybersecurity, that can be a mistake.
For decades, trains ran on hardware and analogue controls or isolated onboard systems with no outside connections. That made them “secure by design.” As a result, older trains are sometimes assumed to be less exposed to digital threats. In reality, their integration with newer systems or reliance on outdated protections can make them vulnerable.
Why older fleets can be a cyber weak spot
As legacy trains are upgraded to meet today’s operational demands – whether to improve passenger experience, boost efficiency, or enable smarter maintenance – digital technologies are increasingly being introduced. These upgrades bring clear benefits, but they also change the cybersecurity landscape.
Segmented networks: Many older fleets still operate on unsegmented networks, where there is no clear separation between different functional systems. Without defined security boundaries, an attacker who gains access to one part of the network can often move laterally across others with minimal resistance.
Outdated technology: This challenge is compounded by outdated software and hardware. Unlike modern systems that benefit from regular security updates, legacy components may go years without patches due to discontinued vendor support, missing documentation, or gaps in maintenance routines. These vulnerabilities can make older fleets an attractive target for cyber attackers.

Cyber risks in depot practices
While train depots often have formal security policies in place – like in many workplace environments – they rely heavily on trust to be effective. Technicians are expected to follow best practices, but cybersecurity can sometimes take a back seat to operational pressures.
Depots are also occasionally overlooked in broader organisational cybersecurity strategies, which means critical controls, such as software access and authentication, may be inconsistently applied. A common example is the use of weak or shared passwords on maintenance laptops. According to IEC 62443 and CLC/TS 50701, strong authentication measures, including complex, unique credentials, are essential for protecting industrial systems. These requirements apply equally to legacy fleets, which often rely on depot-based diagnostics and updates.

Securing the supply chain
A major risk to both new and legacy fleets often comes from suppliers. While TOCs maintain strict security protocols for managing third-party vendors, gaps can emerge from external suppliers.
Rail systems often depend on external vendors for hardware and software support. However, many of these suppliers may not prioritise cybersecurity to the same extent as those operating or owning the trains. To mitigate this risk, it is essential to ensure that suppliers follow the same stringent security practices when accessing your networks and systems.
Summary: Top cyber risks for legacy fleets
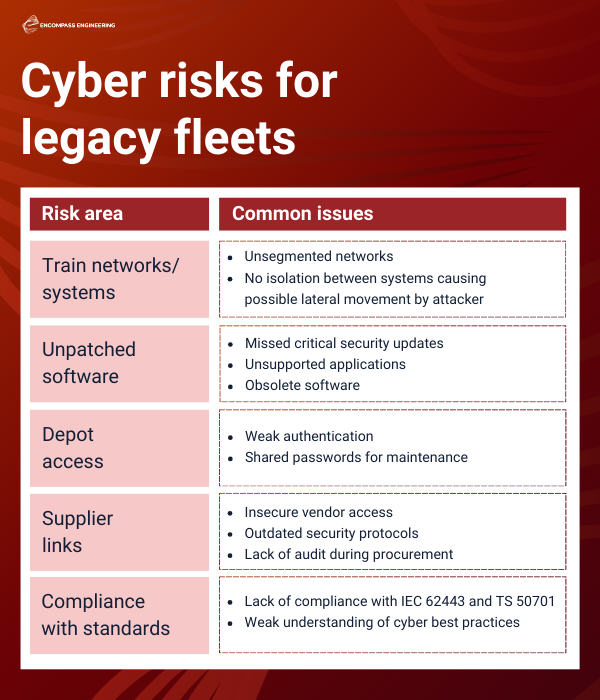
As rail operators invest in modern fleets with advanced digital systems, legacy rolling stock is often overlooked from a cybersecurity perspective.
Yet older trains can pose significant risks. Many were not designed with cybersecurity in mind and may run on unsegmented networks, giving attackers easier access. Ageing software and a lack of updates further expose critical vulnerabilities.
Risks also extend to depots, where inconsistent security practices and weak vendor controls can leave systems open to attack.
Protecting legacy fleets requires a comprehensive strategy that includes system updates, secure maintenance, and supply chain security – all underpinned by evolving standards, such as TS 50701 and the upcoming IEC 63452.
Ready to improve your cyber resilience?
Cybersecurity threats are a growing concern for the rail industry, and protecting your systems is essential for safe and reliable operations.
At Encompass, we help operators and train owners gain a clear understanding of their systems’ vulnerabilities and the risks they face, empowering them to build stronger cyber resilience. Learn more about our approach to cyber assurance for rail.